PureSNAT - Linux SNAT Kernel Module

January 2015
support@pureload.com
PureSNAT - Linux SNAT Kernel Module
|

|
| PureLoad
5.2 January 2015 |
http://www.pureload.com support@pureload.com |
In some cases, performance tests require the use of many IP
addresses in order to test under realistic conditions. This can be
accomplished by configuring the OS on the PureLoad Worker machines
to have multiple IP addresses. For larger tests this can become
impractical and limited by what the OS can handle. Source Network
Address Translation (SNAT) can be used in order to achieve a much
higher number of IP addresses and a more efficient handling of IP
packets.
PureSNAT is a kernel module for Linux which allows PureLoad to
perform SNAT of IP packets on the local machine. It supports both
IPv4 and IPv6. Outgoing packets get their original source
addresses replaced with different addresses to be used in the
test. Incoming packets are translated back and delivered to the
original IP socket. Using this technique, it is possible to use a
large number of IP addresses without having to configure them in
the OS.
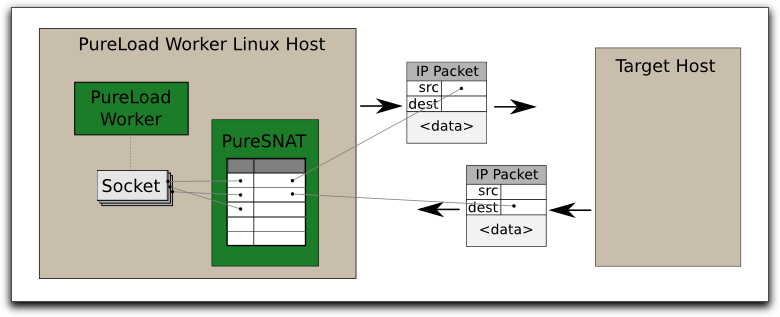
For each socket that is created by the PureLoad Worker, PureSNAT
will hold an entry in a translation table so that it can perform
the address translation for outgoing and incoming IP packets.
The PureSNAT package contains the following files:
| puresnat.ko
kernel
module
binary
file libpuresnat.so Java native library psnat command line binary executable |
| %> sudo insmod puresnat.ko |
| %> lsmod Module Size Used By puresnat 115105013 0 ....... { other modules } ....... %> tail -2 /var/log/messages Jun 11 10:54:36 PureUbuntu1204 kernel: [19261.524645] PureSNAT module version: 1.3 loading.... Jun 11 10:54:36 PureUbuntu1204 kernel: [19261.525533] PureSNAT module version: 1.3 loaded |
| %> sudo ip route add 192.168.16.0/24 via 192.168.1.23
dev eth1 |
| %> sudo ./psnat -connect 192.168.1.23 192.168.16.10
192.168.1.44 8080 Connection successful: 192.168.16.10 => 192.168.1.44:8080 |
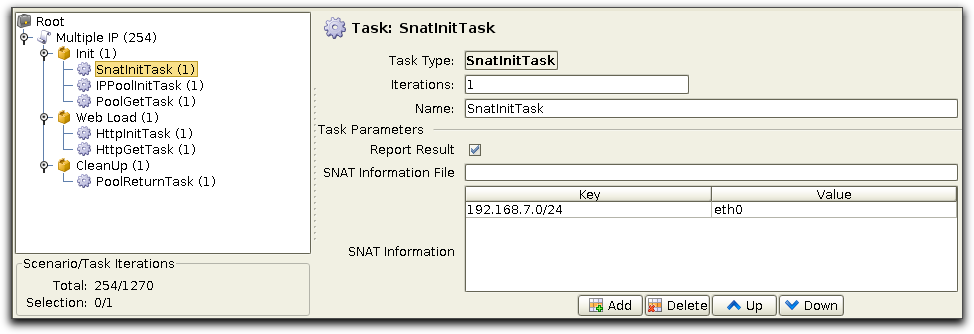
Note: PureLoad Manager must be executing as root in order to be able to
use PureSNAT.
| %> sudo ./psnat Usage: psnat <cmd> Command: -stats print statistics (stdout) -snat_on enable SNAT log -snat_off disable SNAT log -frags_on enable fragment log -frags_off disable fragment log -print_snat print SNAT tables -connect <orig src ip> <new src ip> <target ip> <target port> -dgram <orig src ip> <new src ip> <target ip> <target port> output sent to /var/log/messages. %> sudo ./psnat -snat_on %> tail -f /var/log/messages Oct 3 17:26:57 ubuntu kernel: [36090.506045] PureSNAT: tcp_v4 log: 1 Oct 3 17:26:57 ubuntu kernel: [36090.506046] PureSNAT: tcp_v6 log: 1 Oct 3 17:26:57 ubuntu kernel: [36090.506048] PureSNAT: udp_v4 log: 1 Oct 3 17:27:04 ubuntu kernel: [36097.599658] PureSNAT: Add TCP SNAT entry IPv4 orig_src=192.168.1.96:43752, new_src=192.168.7.1:43752 Oct 3 17:27:04 ubuntu kernel: [36097.599849] PureSNAT: sent TCP SNAT packet IPv4 orig_src=192.168.1.96:43752, new_src=192.168.7.1:43752 |
The settings can also be changed using sysctl with the
following variables:
| %> sysctl -a | grep puresnat net.puresnat.log_frags = 0 net.puresnat.log_tcp_v4 = 0 net.puresnat.log_tcp_v6 = 0 net.puresnat.log_udp_v4 = 0 |